The three pillars of provenance that make up durable Content Credentials
Content Credentials help users make informed decisions about whether to trust content by providing context about its provenance. For example, they show where an image came from and how it was made.
They can act as attribution, helping creatives gain recognition for their work. And they can also give creatives more agency over how their work is used, because when creatives apply Content Credentials, they can ask AI models not to train on their content.
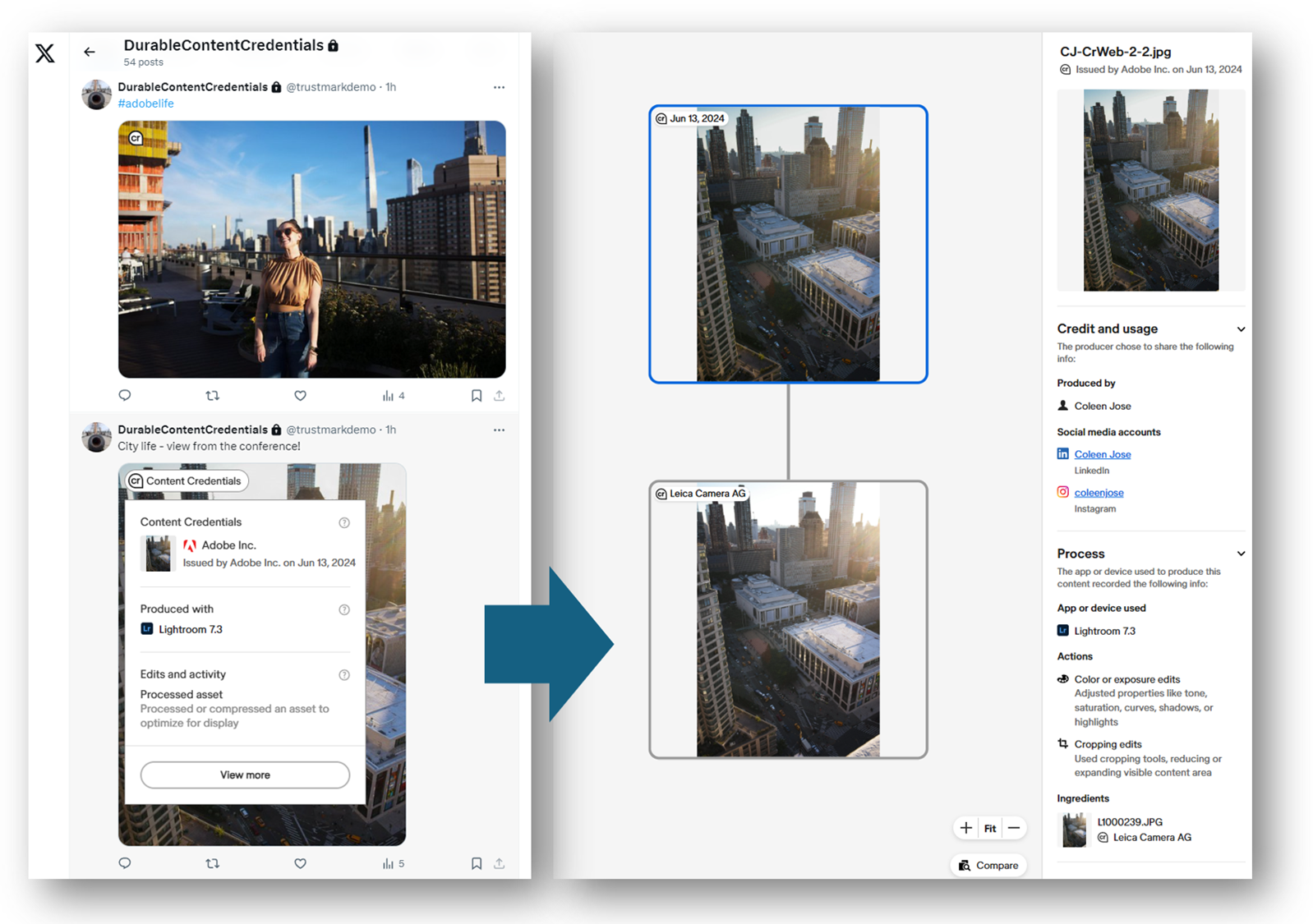
All of this is possible because of the metadata embedded in Content Credentials. But what happens when content platforms strip this metadata away? Despite widespread adoption of Content Credentials, including by platforms like LinkedIn and TikTok, it is still common for social media and content platforms to remove metadata.
Durable Content Credentials are the solution to the metadata stripping problem, because they create permanent provenance that follows an image wherever it goes.
Creating durability with metadata, watermarking, and fingerprinting
We are delighted to announce the publication of our scientific journal paper in the May-June issue of IEEE Computer Graphics and Applications, describing how durable Content Credentials work using the “Three Pillars of Provenance.”
Durable Content Credentials use invisible watermarking to embed an identifier in an image. The identifier can be used to look up and recover metadata if it is stripped away by content platforms. To perform watermarking, Adobe has developed TrustMark, a state-of-the-art invisible watermarking algorithm that can survive processing by content platforms in a way that metadata cannot. To accelerate adoption, Adobe has released TrustMark as open-source software under the MIT license.
Our IEEE paper describes how TrustMark may be combined with image fingerprinting in order to safeguard against credential spoofing. In doing so, durable Content Credentials unify three technology pillars: metadata, watermarking, and fingerprinting. This triad of technologies mutually support one another to create permanently attached Content Credentials.
For example, Content Credentials metadata is cryptographically secure but easily stripped — a property countered by the persistence of robust invisible watermarks in content platforms. The ability to spoof (i.e., copy or fake) a watermark is countered by visual matching performed by a cryptographically signed image fingerprint within the Content Credentials.
Discover the potential of Content Credentials to build trust and drive value
Our paper also outlines how, in the future, provenance technologies such as durable Content Credentials can be extended beyond Adobe’s implementation to enable distributed lookup of stripped Content Credentials across multiple providers. It also discusses how authentic content supported by durable Content Credentials has the potential to unlock value creation in new ways, for example by tracing and rewarding the reuse of media within the creative economy.
Explore the paper to learn more about how Content Credentials are helping to usher in a new era of trust and transparency in the digital landscape.