When Russia’s invasion of Ukraine began in February 2022, many of us were tuned to news reports showing evolving maps of Russian troops massing on Ukraine’s borders. In the weeks that followed, on social media, authentic and inauthentic videos of the unfolding conflict proliferated.
One video clip on TikTok showed a paratrooper filming himself descending on a field. He spoke Russian while recording other paratroopers from a short distance, which countless users interpreted as Russian soldiers landing in Ukraine. The clip received 1.3 million likes and was shared over 136,900 times on the platform, according to an archive of the viral video. Reuters reported it was later traced to an Instagram post published in 2015.
This brought me back to a question among my journalist colleagues when we were reporting breaking news: would you rather be first or accurate? We set off in the early 2010’s when news reporting was increasingly paired or replaced with user-generated content. Social platforms were just emerging in popularity. The United States had yet to experience the weaponization of mis- and disinformation on platforms, eroding trust in our news and visual information ecosystems.
Pre-bunking with provenance
Manipulated content and false narratives like Russian paratroopers supposedly landing in Ukraine or more recent and prevalent examples are countered with fact-checking workflows and detection technology. But verification of content online is often established days or weeks after viral mis- or disinformation has made its rounds across platforms, political commentary and dinner table conversation.
In October, the Content Authenticity Initiative (CAI) announced partnerships with Leica and Nikon to implement digital provenance technology into cameras, enabling attribution for creators at the point of capture while providing transparency about the facts and origins of a piece of digital content. This milestone was made possible by the CAI’s open-source SDK that implement the technical specification developed by the Coalition for Content Provenance and Authenticity (C2PA).
Tim Murphy and Erin Oberhauser, co-founders of Pixelstream, are at the forefront of developer implementation with the open-source tools. Since it was released in June this year, they’ve been busy exploring how to authenticate content with automation, user experience and security at the product’s core.
“We were watching early coverage of the invasion of Ukraine, listening to reporters discuss how they handled content from journalists and citizens on the ground,” Tim said.
“They described how their team attempted to authenticate the videos, a manual process that would be prone to human error,” he continued. I recently spoke to Tim and Erin to discuss their journey and motivation to expand authentication access, help build trust and transparency online and how developers may contribute to the work ahead.
This interview has been edited for length and clarity.
Coleen Jose: What motivated you to join the Content Authenticity Initiative?
Tim Murphy: Observing how individuals were capturing important, historic events inspired us to be part of the CAI. Yet, when those images or videos are shared on their websites or social media, they don’t always carry the same weight as when a large media company publishes content.
Today, consumers of media rely heavily on the reputation of established brands to determine authenticity. With the C2PA specification, and the CAI open-source implementation of that specification, we now have a path forward for journalists and individuals to display the same trust signals as large media companies. That said, large media companies also face significant challenges with authenticating the content they receive or wish to share from social media.
CJ: What is Pixelstream? Who do you want to reach and how do you want them to use it?
TM: Pixelstream is a version-controlled sharing platform for authentic media. It’s kind of like GitHub for authentic media assets, but it’s built on top of C2PA tooling instead of Git. This allows you to share media with your team or with the entire world while leveraging the transparency, attribution, and trust you get with C2PA.
Sharing on Pixelstream is different from posting something to social media, though. When you publicly share your content on Pixelstream, people and organizations can “fork” the media from any point in its provenance. This means they can make edits to their copy using full resolution assets right on Pixelstream or with software like Photoshop.
It’s kind of like GitHub for authentic media assets, but it’s built on top of C2PA tooling instead of Git.
Tim Murphy
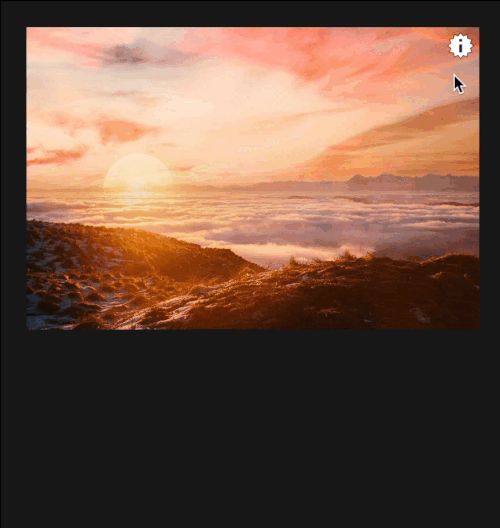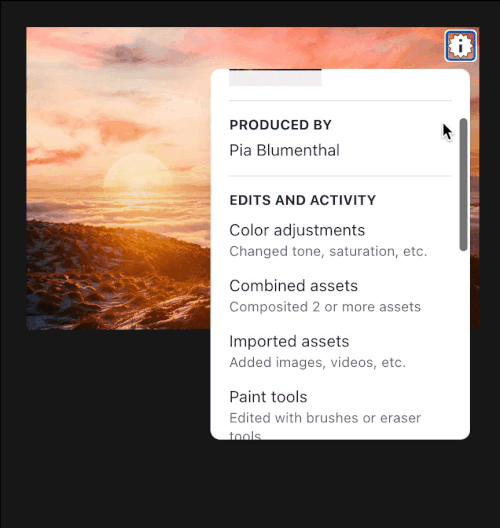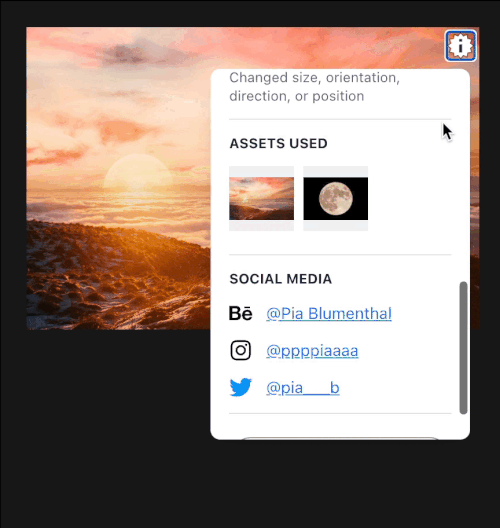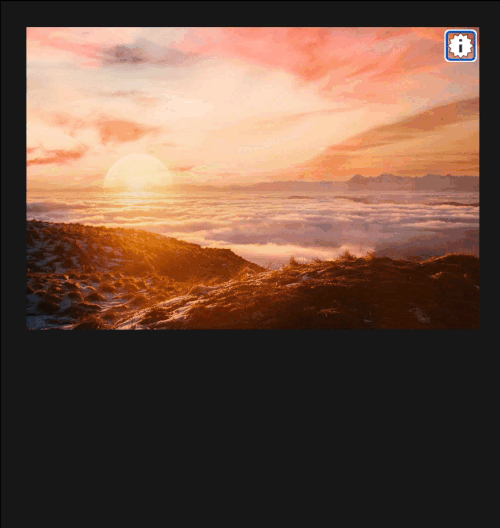
Attribution and edits are automatically bound to the media every step of the way for both the original creator and future editors. This happens with the full power of C2PA transparency and privacy mechanisms. If a media organization is interested in publishing images or video that have been posted to Pixelstream by a user, not only can they authenticate the media through its secure provenance, but they also have access to the original resolution assets should they need to make production edits.
When it’s time to ship, you can easily deploy the authentic production assets and remote manifests on our CDN. We also streamline the process of creating responsive authentic images, and those can be optionally used with our Vue plugin. You can also customize the granularity of your version history on publish. This is useful for merging multiple working versions of an image into one manifest to publish while still accurately tracking the edits and activity.
Lastly, you can use our version control system without sharing any permissions, much like a private repository. This will be a common use case.
Videos courtesy of Pixelstream
CJ: Tell us a bit about your background and the technical problems you’re solving.
TM: Pixelstream was originally started as a side project last year to make it easier for creative professionals and developers to share and deliver version-controlled media assets to production. After seeing how challenging it was to manually authenticate media, we started researching ways to build an automated authenticity feature on our platform. We explored various possible solutions like using existing metadata formats and dynamic digital watermarking.
These approaches had specific shortcomings when it came to being tamper-evident and having a trust model, among other issues. In the case of digital watermarking, we didn’t like the idea of manipulating pixel data for the purpose of encoding data, even if it wasn’t visible. It just seemed like the wrong tool for the job. When we first read about C2PA, it was an obvious solution for the authenticity feature we wanted to add. What we didn’t expect was that the manifest store concept was going to work so seamlessly with the way we had implemented our version control system for media. It’s almost like C2PA was built for a version control system.
Initially, the complexity of the C2PA technical specification gave us some pause, but since a lot of C2PA is built on existing standards, there were a lot of resources available. It did take several reads and plenty of research to get our heads around it, especially some of the PKI aspects. As a two-person team with no funding, we weren't sure we’d be able to put together the engineering resources to implement it. That’s why the CAI open-source tools are critical. Small teams would probably struggle to implement C2PA without the toolkit.
CJ: How did you get started with the C2PA tool to verify and explore content credentials?
TM: We originally got started with the tools after attending the CAI Virtual Workshop in June of this year. After the event, we decided to start with the toolkit because we were most interested in adding manifests to assets. If we’re being totally honest, we really wanted to see the Verify site display “Signed by Pixelstream” when we uploaded an image from our platform. There was something really special about seeing that.
So, we installed the C2PA tool and used the sample files to add a manifest to an image. It worked, but of course, it didn’t say that it was signed by Pixelstream. We needed to write our own manifest definition files and generate our own test key and certificate chain. We have found certificate management to be the most difficult part of the journey. Fortunately, the CAI team has been super engaged on Discord, helping people through this part.
CJ: Tell us about what you’ve released.
TM: In September, we released a free online version of the open source C2PA tool that allows you to add manifests to an uploaded source file and optionally upload a parent file, much like the CLI version of the C2PA tool. The manifest definition file is automatically made for you with user specified CreativeWork and action assertions. We built this as a utility to help us with building and testing our main platform and thought it might be helpful to other people getting started with CAI tools. We have pushed one major update to the tool since September and intend to add additional features in the future to eventually fully mirror the CLI version. You can check it out here.
JavaScript SDK
Everything you need to develop rich, browser-based experiences with content credentials. View here.
C2PA Tool
Install this tool to create, verify and explore content credentials on the command line. View here.
Rust SDK
Develop custom applications across desktop, mobile, and services that create, verify, and display content credentials via our Rust library. View here.
We also released an open-source MIT licensed plugin for the Vue.js JavaScript framework. It is built on the CAI JavaScript SDK and works with any images that contain content credentials, including from Photoshop. You can install it via NPM and it takes just a few lines of code to add it to your app. From there, you can use the component just about like an ordinary HTML <img> tag. In addition, it supports responsive images via the srcset attribute. This means that it automatically updates the content credentials when different versions of a responsive image are displayed.
We originally built the plugin to display images on our sharing platform, but we quickly realized that it would be useful to our CDN users and any other Vue.js developers that need to display content credentials. You can check it out in our GitHub.
CJ: How should people contribute to your project?
TM: With the Pixelstream platform, anyone interested in being an early tester can sign up for our mailing list. Because C2PA is so new, we are going to have to learn a lot from our early users.
When it comes to the open-source plugin, the most helpful thing would be for people to install it and create issues on GitHub if they run into problems. We released that pretty early so by the time our main platform is out, hopefully the plugin will be well tested.
CJ: What advice do you have for other developers who are just getting started with the toolkit?
TM: The best advice that we can offer other developers is to start with the SDK that uses the programming language most familiar to you. For instance, we probably should have started with the JavaScript SDK because our platform is written with JavaScript. That may have been easier while we were learning the C2PA terminology. Also, join the CAI Discord because the team is incredibly responsive.
CJ: What’s next?
TM: Up next for us is finishing our early release, onboarding our first users, and beginning work on the Pixelstream iOS app. Then, we’ll need to think about funding in order to build this out for general availability. This is an ambitious project, but we are incredibly motivated by the mission and the technology.
More from Pixelstream